SSH Secure Shell is a network protocol, its primary purpose is to allow you to securely connect to a remote system over a network. Using SSH you can connect to the remote system using username and password based authentication or using a key-based authentication. In this tutorial, you will learn to setup key-based authentication on a Linux based system.
Why use key-based authentication, what are the advantages?
Public key authentication is more secure than password-based authentication Make it difficult for hackers to break into your system due to a weak password Another layer of security is available by adding a passphrase, as it can be left out blank Forcing key authentication allows you to disable password authentication which in effect prevents brute force attacks
Steps to setup key-based authentication on a Linux computer
1. Generate SSH Key Pair on the client machine
On the client machine run the following commands to generate SSH keys:cd ~/.sshssh-keygen -t rsa
When asked for passphrase, leave it blank or enter your desired passphrase. Having a passphrase makes automation difficult for some of the processes. Output of the above command will look something like the following:
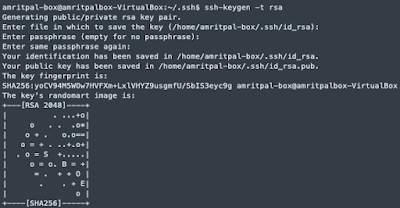
2. On server machine create an SSH folder
mkdir -p ~/.ssh/
3. Copy public key file from client to the server machine
Run the following command on the client machine to secure copy id_rsa.pub file to the remote machine:scp -P "ssh-port" ~/.ssh/id_dsa.pub username@serverip-address:~/.ssh
4. On server machine append public key to authorized keys file
cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys
5. On server machine change authorized keys file permissions
chmod 700 .sshchmod 600 .ssh/authorized_keysrm .ssh/id_rsa.pub
6. Successfully done, test your result
On the client machine run the following command to verify correctly logging onto server machine using private SSH key:ssh -P "ssh-port" username@serverip-address
References
https://devops.profitbricks.com/tutorials/secure-the-ssh-server-on-ubuntu/
https://www.ssh.com/manuals/server-zos-product/55/ch06s02s02.html
https://debian-administration.org/article/530/SSH_with_authentication_key_instead_of_password